The following article was also published on DZone and you can read it here.
Man has this innate need to reinvent and evolve. To constantly innovate and grow.
His urge to progress drove him to spark fire from stone, get wheels rolling with wooden spokes, illuminate dark corners with electricity, and now muse over a Hyperloop traveling at 600 mph. The current phase of his evolutionary thirst happens to be in the digital arena, originating from the elementary step of digitization to a pivotal era of digital transformation.
A quick distinction between the two digi terms – While digital transformation implies rethinking and rebuilding a new business model, digitization happens to be a means or to word it better a “start” towards being digitally transformed.
After all, if your company’s assets lie bound in papers and bulky files, they remain as mere souvenirs, valuable yet futile.
What started as a novel initiative by a handful turned out to be a matter of urgency, as confirmed by the Forbes Insights and Hitachi survey where 50% of the 573 top executives surveyed consider digital transformation as the top strategic priority and their top investment priority is unsurprisingly for new technologies in digitization and data analytics.
Caution! Traps and Pitfalls Ahead
But, along with any wave of innovation comes its own baggage of fears and scares. Disastrous damages caused by fire and vehicles claim precious lives and countless properties around the globe. A similar hazard lies in the digital transformation journey – cyber threats and attacks.
If thieves are waiting to access your critical information in the physical world, then they are very much present in the digital business to steal valuable data and spoil your reputation. Considering the pace at which digitization is moving, a research by Juniper predicts that the cost of data breaches will rise to $2.1 trillion by 2019. The rampant Wannacry attacks in May 2017 that brought factories and hospitals to a halt in over 150 countries and incurred losses of about $4 billion, rightly substantiates the prediction.
We just started digitization. So isn’t it too early to think about security concerns?
Whenever there’s a novel technology adopted massively by various businesses, they inevitably become the sweetest spots for information security attacks. Take for example the hot trend of 2017 – IoT, whose investments are projected to be at a whopping $86 Billion. Though the market for IoT devices gained huge momentum in 2017, the initial tone for connected things was set in 2016. And October 2016 saw the notorious Dyn cyberattack in which millions of IoT enabled cameras and DVRs fell prey for the severe blow of Mirai infections, creating multiple Denial-of-Service attacks. An immense setback to the IoT technology even before it could stabilize in the market.
Another case of threat in the budding stages of novel technologies would be that of Ethereum – an open-source platform built on the blockchain technology to create and deploy decentralized applications. Just when investors started cashing in for the Decentralized Autonomous Organization, an organization that runs through smart contracts implemented via Ethereum, a cyber burglar managed to siphon $50 Million to his account in June 2016. The following year saw 2 more Ethereum hacks which got the developers hard-fork the Ethereum cryptocurrency – Ether.
I could go on about how the ransomware attack on the San Francisco Municipal Transit Agency’s payment systems gave a free ride for passengers, the Petya attacks brought many European and US companies including shipping enterprise Maersk to a halt, the shocking Equifax data breach that exposed personal information of up to 143 million Americans, and many many more. These attacks were all targeted to gain monetary benefits, steal data and more commonly sabotage a company’s reputation and ultimately ruin businesses.
High-time to intensify your security stance
Enough and more instances for businesses looking towards digital transformation to get quite serious about information security. Any business – big, medium or small must take realistic steps towards securing their digital assets. In fact, startups and flourishing SMBs are found to be easy and likable targets for hackers with 61% of all data breaches in 2017 occurring in organization with less than 1000 employees.
Sounds intimidating, right?
The very realization of the scare is the first step towards establishing your business’ security posture. Remember that you cannot secure your organization 100% neither there is one best solution/product that can keep your information security fears at bay. However, what you can do is minimize the chance of an attack or the losses thereafter, right from the time you dive into digitization efforts and move towards digital transformation
Don’t forget to get the basics right!
A good point of reference for your attempts at securing your digital business would be 20 Critical security controls proposed by the largest source for information security training – SANS Institute . A broad categorization of the controls would be –
- Risk and Asset Identification and Management – Since the volume of data you own is phenomenal, identifying and grading the risk levels of the information you possess helps in deploying the right security feature. Identify and maintain an inventory of all the devices and software that access or store or in any way contact your company data. Secure configuration, frequent vulnerability assessment, and software/firmware updates of these assets are a huge put-off for hacker intrusions. Clear segregation of server access in test and production environments help in limiting and containing the risks observed.
- Borderline security – Organisations are undoubtedly exposed to websites which often hold phishing traps to unsuspecting users. Internet gateways and firewalls being properly configured provide an elementary level of defense around the organization’s perimeter. Though the use of firewalls as a security device is being questioned, it does prove its part in fending malicious outsider IPs and dubious port usages.
- Strong Endpoint Protection – Digitization and digital transformation, on the whole, involves the total revamp of the underlying business model which by default includes every member of an organization, who in turn are in direct contact with your digital assets. Securing the assets through which they access the corporate network (both onshore and offshore) becomes an absolute must.
These endpoint assets include PCs, laptops, smartphones, PoS terminals and other remote devices. Going more than mere signature-based antivirus patches pushed once a week is needed to defend zero-day threats and unreported vulnerabilities. Steps like restricting USB access, blocking user-enabled random software installations and preventing access to black and greylisted sites, when applied org-wide goes a long way in keeping off cyber attacks via employee endpoints.
- Reliable backup and data recovery capabilities – Disastrous malware families especially ransomware are aimed at disrupting the availability of data. A huge sum of money is then demanded to restore the data, though the vow is never kept in most cases. A regular backup of your critical data right from the beginning of your digitization journey saves the headache of being crippled at the loss of data. Make sure to ensure that all your recent data is safely duplicated and lock it away in a location other than where your primary data is stored.
- Detect, respond and Mitigate Intelligently – Capture, store, and analyze logs from critical infrastructure like firewalls, Intrusion Prevention systems, endpoint protection software, servers in order to monitor, detect and respond to abnormal activities in your enterprise network. Security Incident and Event Management (SIEM) tools are available in the market to centrally manage the incident detection and response actions at real-time.
Traditional SIEM ways are now being upgraded to support predictive analysis of abnormal activities which will prevent an incident from happening in the first place. Robust threat modeling and actionable threat intelligence ventures are further steps in improving a company’s security posture.
Note: Incident here refers to any event that has breached the security policy of a company and an abnormality refers to a suspected event which may lead to an incident.
Apart from taking these fundamental measures, whenever your organization implements a new technological advancement, securing it should be a top priority. Let’s say you’ve recently adopted a cloud-based solution or had IoT enabled cameras installed in your premises, shielding them from attackers has to be taken care of at once.
But bare minimums need to evolve as your business grows
A checklist of 20 odd security initiatives isn’t enough to keep your reputation from tumbling down due to a cyber attack. The more successful and accessible your organization becomes, the more rigorous are the effort to disrupt your services! And what better way to do it than stealing your information or performing a Denial of Service attack on all your servers.
So how and when do you turn up the notch in your information security undertakings? The answer to the “when” part of the question depends on which level of digital maturity your organization is in.
As outlined by Gartner’s security score levels, it begins with initially being aware of the risks presented by cyber threats and taking primitive defense actions, to appointing a Chief Information Security Officer (CISO) who makes sure security policies are well-defined and develops a proactive, user-responsible approach towards a secure organization.
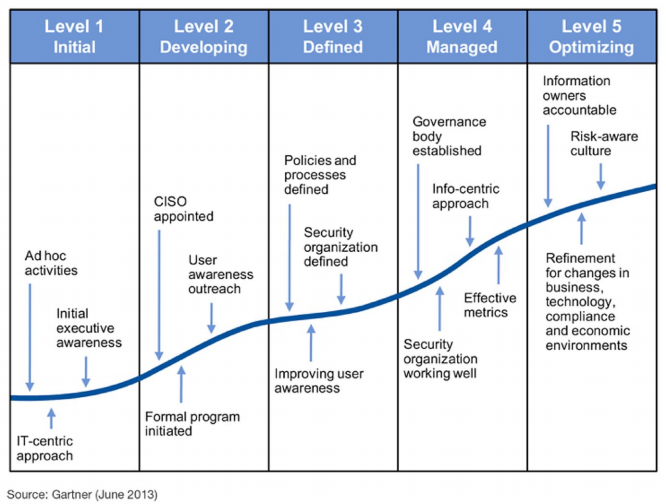
It is important to note that the maturity steps are not reserved to elite, large organizations but must be adopted by any company that has planned/gone down the digitization path. A 2016 state of SMB cybersecurity report by Keeper security shows that 50% of SMBs were breached in 2016 alone which is not surprising as 82% of small business owners underestimate the risk of their assets and think they are not prone to attacks.
Foster a Security-aware culture in your enterprise
Even the most sturdy cybersecurity solution of your company cannot stop threats that arise due to inadvertent human errors. A recent study reveals that about 58% of cyber threats arise from the extended enterprise (employees – 33%, ex-employees – 7% , and trusted partners – 18%), giving a clear indication that the responsibility to safeguard a company’s digital assets lies in the hands of everyone working in a company.
Falling for phishing emails that exploit unknown vulnerabilities, exposing source codes on public repositories, failing to practice coding best practices, treating domain passwords lightly are few instances of how careless acts by employees can incur irreparable losses. Organisations must come up with creative ways to involve, instruct and inculcate a security-aware environment in all their business dealings.
Agreed that the digital world is brimming with scammers and spammers. But, don’t let the terrors of the cyber world snuff your dreams of innovation and reinvention. Digital transformation has become the core business goal of many executives, driving them to rethink and remodel the way they interact with their customers and employees.
Embrace the security challenges in your digitization journey with the same vigor, so that you will be ready to tackle growing cyber threats and skip the embarrassment faced by Yahoo! and Target. Have fun innovating!
Read AI-generated summary
- The current phase of his evolutionary thirst happens to be in the digital arena, originating from the elementary step of digitization to a pivotal era of digital transformation.
- A quick distinction between the two digi terms – While digital transformation implies rethinking and rebuilding a new business model, digitization happens to be a means or to word it better a “start” towards being digitally transformed.
- What started as a novel initiative by a handful turned out to be a matter of urgency, as confirmed by the Forbes Insights and Hitachi survey where 50% of the 573 top executives surveyed consider digital transformation as the top strategic priority and their top investment priority is unsurprisingly for new technologies in digitization and data analytics.
- Another case of threat in the budding stages of novel technologies would be that of Ethereum – an open-source platform built on the blockchain technology to create and deploy decentralized applications.
- I could go on about how the ransomware attack on the San Francisco Municipal Transit Agency’s payment systems gave a free ride for passengers, the Petya attacks brought many European and US companies including shipping enterprise Maersk to a halt, the shocking Equifax data breach that exposed personal information of up to 143 million Americans, and many many more.